Under which cyberspace protection condition is the priority? The answer lies in understanding the critical nature of safeguarding our digital realm and prioritizing measures that effectively mitigate cyber threats. This article delves into the concept of cyberspace protection conditions, their significance, and the essential factors to consider when determining their priority.
Cyberspace, the interconnected network of information and communication technologies, has become an integral part of our lives. As we increasingly rely on digital platforms for communication, commerce, and critical infrastructure, the protection of cyberspace becomes paramount. Cyberspace protection conditions encompass a range of measures and strategies aimed at safeguarding cyberspace from malicious actors and threats.
Cyber Security Protection Conditions
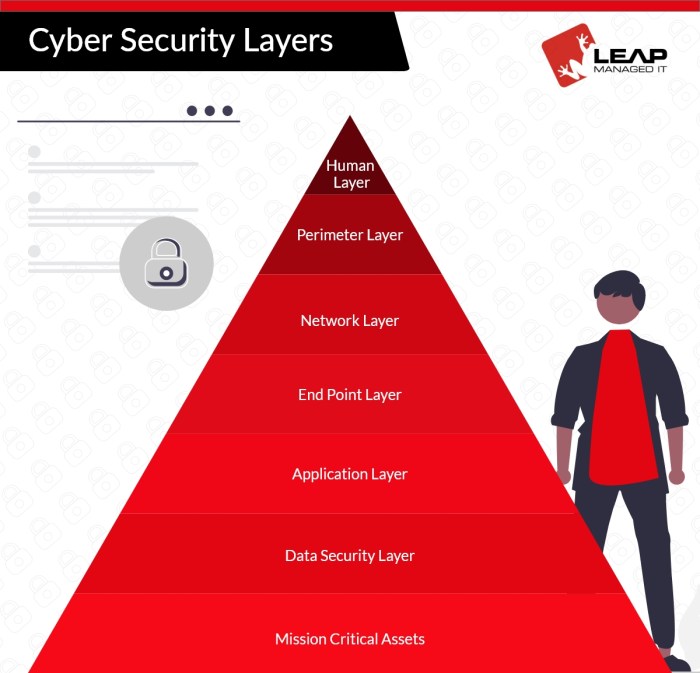
Cybersecurity protection conditions refer to the specific criteria or guidelines that are established to ensure the protection and integrity of cyberspace and its various components, including networks, systems, data, and information.
Types of Cyber Security Protection Conditions, Under which cyberspace protection condition is the priority
- Confidentiality:Ensures that sensitive information remains private and is only accessible to authorized individuals.
- Integrity:Protects data and systems from unauthorized modification or corruption.
- Availability:Ensures that systems and services are accessible and operational when needed.
- Accountability:Tracks and records user activities to establish responsibility for actions and events.
- Non-Repudiation:Prevents individuals from denying their involvement in a transaction or communication.
Priority of Cyber Security Protection Conditions: Under Which Cyberspace Protection Condition Is The Priority
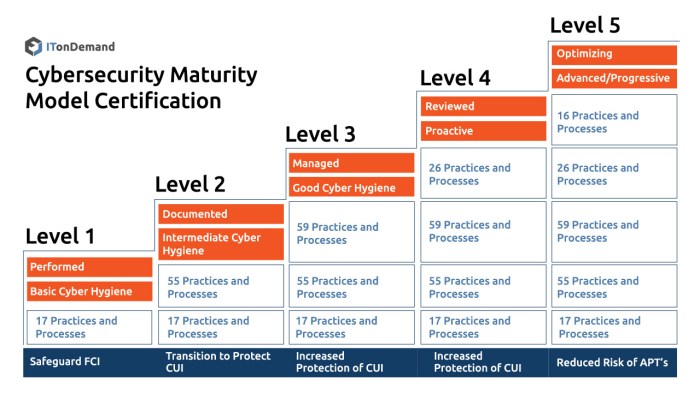
Prioritizing cyberspace protection conditions is crucial to effectively allocate resources and ensure the most critical aspects of cybersecurity are addressed. Factors to consider when prioritizing include:
- Impact on Business Operations:Conditions that impact the continuity and functionality of critical business processes should be prioritized.
- Regulatory Compliance:Compliance with industry standards and regulations can guide prioritization efforts.
- Risk Assessment:Identifying and evaluating potential threats and vulnerabilities helps prioritize conditions that need immediate attention.
Methods for Assessing Cyber Security Protection Conditions

Various methods can be used to assess cyberspace protection conditions, including:
- Vulnerability Scanning:Automated tools that identify known vulnerabilities in systems and networks.
- Penetration Testing:Simulated attacks to evaluate the effectiveness of security controls.
- Compliance Audits:Reviews of systems and processes to ensure adherence to security standards.
- Risk Assessments:Analysis of potential threats and vulnerabilities to determine the likelihood and impact of cyberattacks.
FAQ
What are the key factors to consider when prioritizing cyberspace protection conditions?
The key factors to consider include the potential impact of threats, the likelihood of occurrence, the cost of implementing protective measures, and the legal and ethical implications.
How can organizations assess the effectiveness of their cyberspace protection conditions?
Organizations can assess the effectiveness of their cyberspace protection conditions through regular risk assessments, vulnerability scans, and penetration testing.
What are some best practices for implementing cyberspace protection conditions?
Best practices include using strong passwords, implementing multi-factor authentication, keeping software up to date, and educating employees about cybersecurity risks.
